This blog is part of a series on Teams. For more articles, check back often
Written: 11/06/2023 | Updated: 10/07/2023
Over the last month we’ve gotten into it on two of the four components of Collaboration Security for Microsoft Teams which were announced back at Secure in March – Attack Simulation and End User Reporting. Both seem really solid adds. I personally think that both are worth the price of the P2 in order to bring this XDR functionality into Teams. So let’s push on and investigate the third component – one which has been part of Exchange Online for some time which is Zero-Hour Auto Purge. Typically known by its acronym ZAP, in the context of Teams it ‘protects end-users by analyzing messages post-delivery and automatically quarantines messages that contain malicious content to stop the actor from compromising the account’. So it is a retroactive automated protection feature which goes after malware, spam and phishing messages. Furthermore ‘once a malicious message is identified, the entire Teams environment will be scanned for that same indicator of compromise and quarantine relevant messages at scale for more effective protection’. Sounds good. Sounds like it’s going to be a real big help to admins who cannot be on hand – or are expected to be on hand – to continuouly monitor their users chats in Teams 24/7. So let’s see ZAP in action. It is currently in preview like the other components and on by default if a P2 licence is assigned and CSTM is lit up via the shell. Of all the components within CSMT this is the one I see changing the least by the time GA comes around since it just works. But having tested the past few days there appears to be some hefty limitations at the time of writing – and ones that as Microsoft 365 admins we need to know upfront even though we know it’s only at the preview stage. One. ZAP only works on private chat and private group chat currently. Channel conversations aren’t supported today. Given that channel messages are housed in shared mailboxes within the Microsoft 365 group construct that’s surprising. But hey, that exactly what happened with loop components so I am pretty sure that will arrive at some point. Two. On the testing I did this weekend it only seems to work for messages within the organisation currently. In other words, no federated chat support for messages sent and received to/from others outside the organisation. That’s probably the biggest limitation here in terms of day to day use or the likelihood of something malicious getting in. Three. During testing I noticed it doesn’t seem to cover meeting chat which is also important, especially if the org allows anonymous users to join meetings. Now, these could be blockers for many organisations. Or they may not be given these orgs could be adding CSMT in preview primarily for the other components. It’ll be important to support all three moving forward, but looking past this the preview does a good job showing you how ZAP works if you have something to test it with.
Let’s go.
This blog will cover
- Enabling Collaboration Security for Microsoft Teams (CSMT)
- Sending a malicious message
- Reviewing zapped teams messages
- Amending the Quarantine policy
- Disabling/Enabling ZAP
Note this blog will have abridged steps which will assume some experience with Teams, PowerShell and a Microsoft 365 Defender environment. A Ring 4 (GA) Test Tenant is used. In addition, a further blog after this one has been written regarding new EXO cmdlets and the new way to manage ZAP settings for Teams via PowerShell under a new Teams Protection Policy which was released early July 2023 and can be read here: Teams Real Simple with Pictures: Configuring Zero Hour Auto Purge (ZAP) for Teams through PowerShell now in Preview. Whilst enabling CSMT, and reviewing zapped Teams Messages remains valid from this blog, I have amended the sections on working with quarantine policies and how to disable and enable ZAP for Teams as this has now changed. These refer to the new blog.
Prerequisites
- Security Administrator (Defender) Exchange Administrator (PowerShell), or Global Administrator permissions
- Latest Exchange Online and Teams PowerShell Modules Installed
- Microsoft 365 E5, E5 Security step up, or Microsoft Defender for Office 365 Plan 2
- This functionality is in preview at the time of writing and is liable to change
ENABLING COLLABORATION SECURITY FOR MICROSOFT TEAMS (CSMT)
At the time of writing this functionality is currently in preview. This initial step of enabling via PowerShell should not be needed in the future
1.) On the Windows Desktop select Start then search for Windows PowerShell. Select Run as Administrator
2.) Install the Exchange Online Module with
Install-Module -Name ExchangeOnlineManagement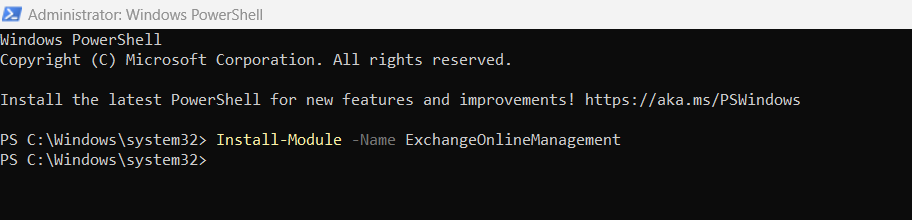
3.) Connect to Exchange Online with
Connect-ExchangeOnline -UserPrincipalName <userprincipalname>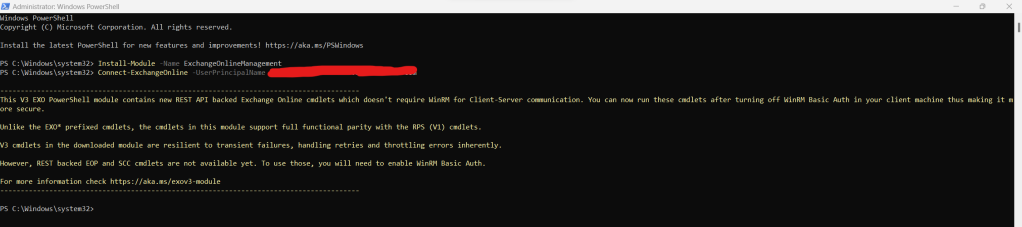
4.) Enable CSMT for onboarding with Microsoft with
Set-TeamsSecurityPreview -Enable $true
5.) You can check back on the status periodically by running
Get-TeamsSecurityPreview
SENDING A MALICIOUS MESSAGE
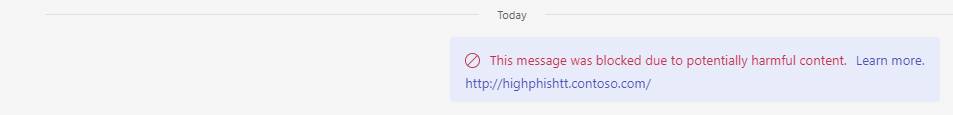
Now that CSMT has been enabled – and assuming ZAP hasn’t been turned off previously within the Microsoft 365 Defender environment it should be on by default and working. So let’s go ahead and send a high confidence phishing message. For this, I will use a phishing link that has been used in several Microsoft demos previously called http doubleslash high phish tt dot contoso dot com (note I am not using the actual link in this blog. It should look like the following image).

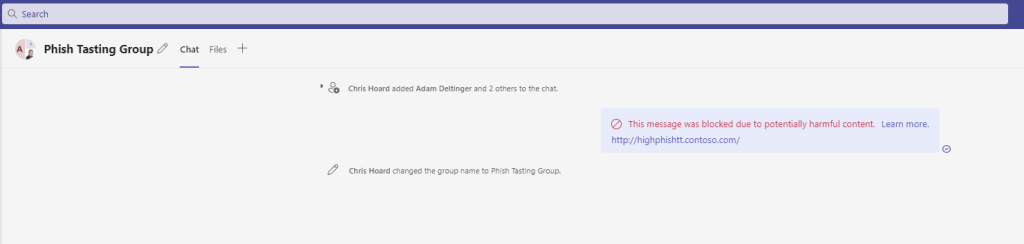
1.) Drop the phishing message into a private chat in Teams. This example is between two users – Chris and Vesku – within the same organisation.
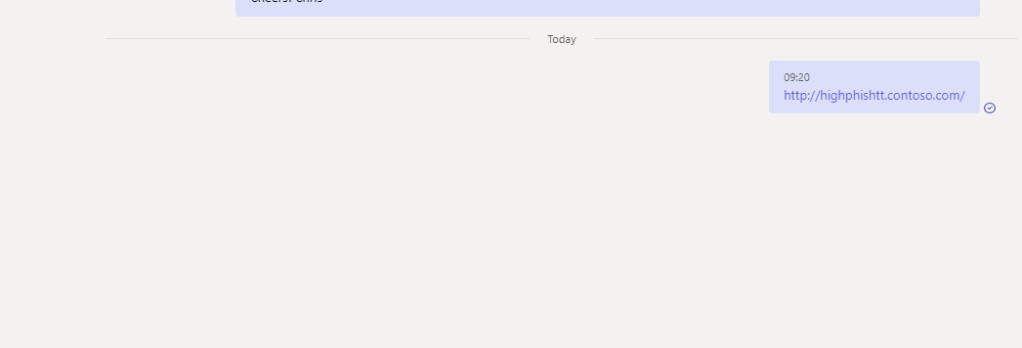
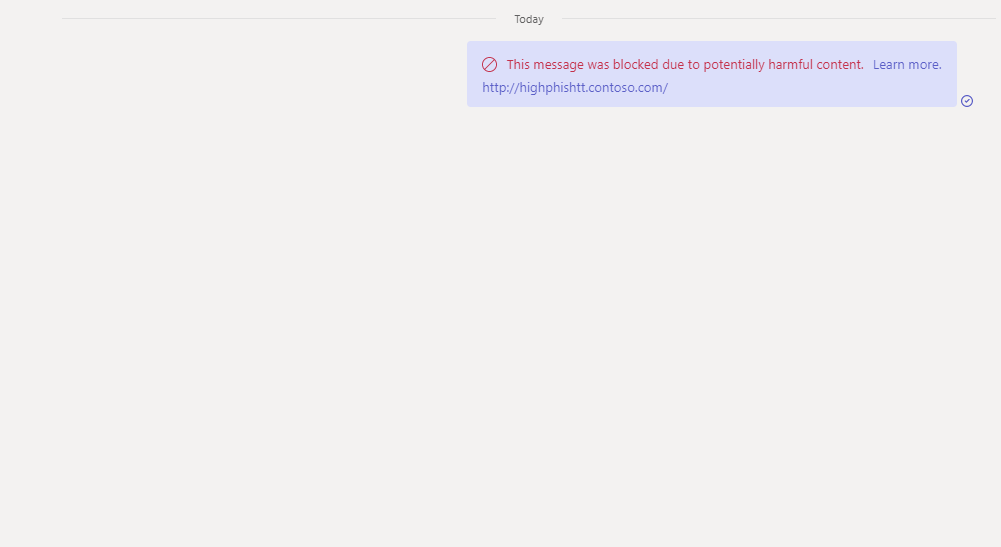
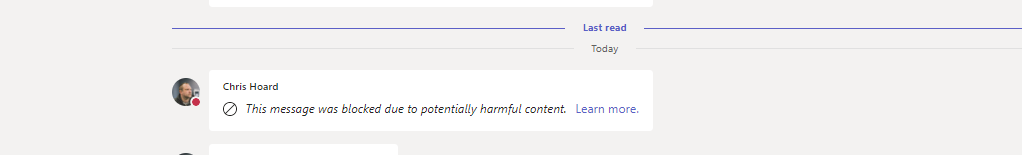
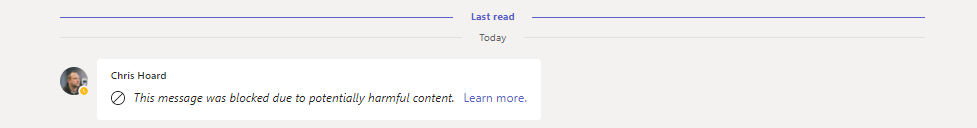
2.) Within about thirty seconds the phishing message gets zapped with the warning ‘This message was blocked due to potentially harmful content’. The recipient does not see the contents of the malicious message.
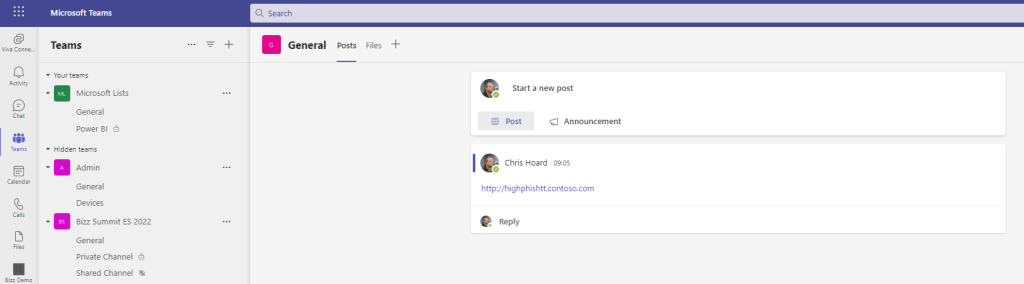
3.) As discussed in the intro dropping the same phishing link into a channel conversation does not get picked up and is a limitation of the preview. I would imagine it will be added in the future, although not being part of Microsoft and the Defender team I cannot confirm that.
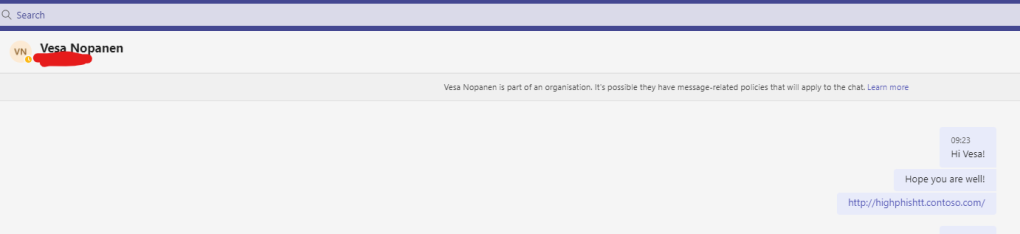
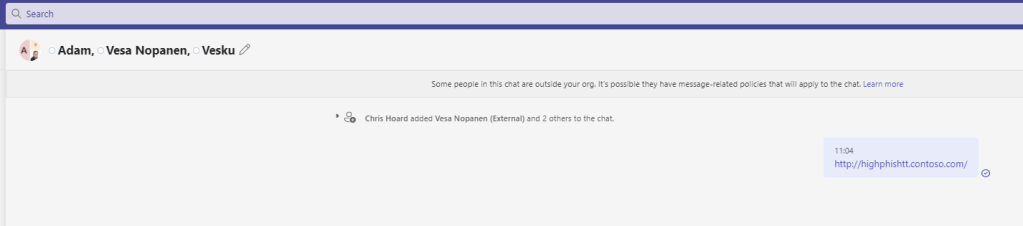
4.) As discussed in the intro dropping the same phishing link into a private chat with users outside the organisation does not get picked up and is a limitation of the preview. I would imagine it will also be added in the future, although not being part of Microsoft and the Defender team I cannot confirm that.
Interestingly, only being able to get it working with org users it’s also consitstent with private group chat. In private group chat with org users the message gets zapped. Ig it includes external users it doesn’t
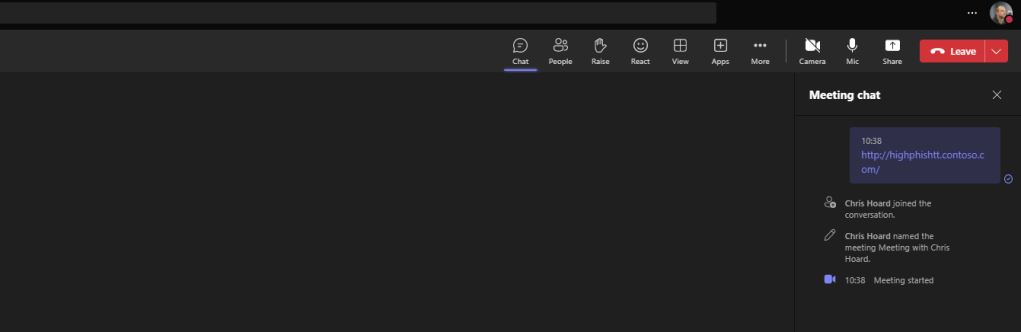
5.) As discussed in the intro dropping the same phishing link into a chat associated with a teams meeting does not get picked up and is a limitation of the preview. I would imagine it will also be added in the future, although not being part of Microsoft and the Defender team I cannot confirm that.
If we understand the scenarios where ZAP is supported today it will help us set expectations, but also look out for additions, perform more testing in the future and feed back to Microsoft.
REVIEWING ZAPPED TEAMS MESSAGES
Now that we have tested scenarios and identified where ZAP is supported, we need to understand where zapped messages can be reviewed by administrators
1.) Login to https://login.microsoftonline.com with administrator credentials
2.) Select Admin from the left app rail, or the waffle

3.) In the Microsoft 365 admin portal, select Show All from the left navigation and then select Security
4.) In the Microsoft 365 Defender Portal select Email and Collaboration in the left navigation and then Review
5.) Select Quaratine
6.) Select Teams Messages
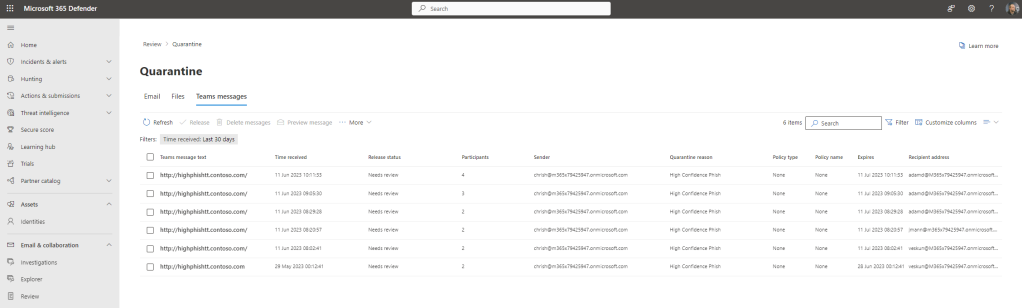
7.) The list of Zapped Teams Messages will appear
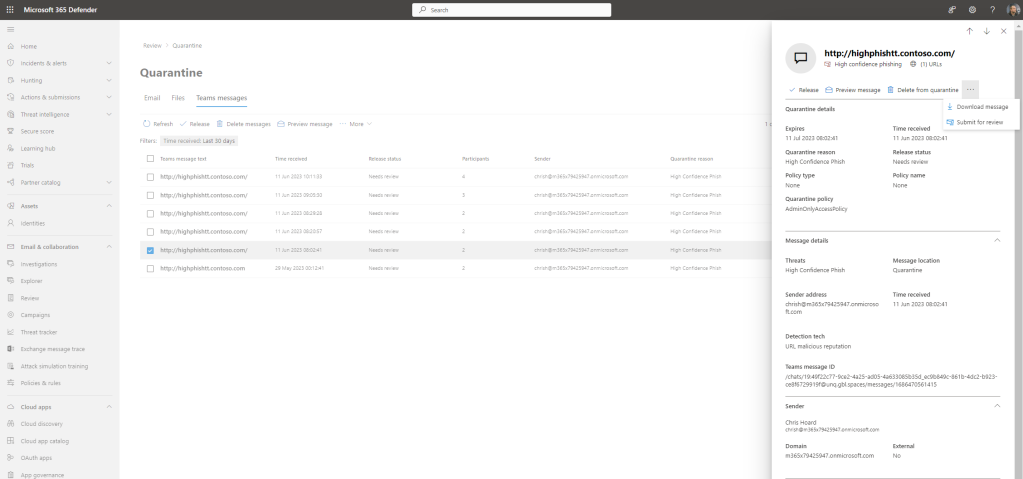
8.) Selecting the zapped mesage, the admin can perform certain actions such as Release, Deleting the Message from Quarantine, Submitting to Microsoft to Review or Previewing the Message
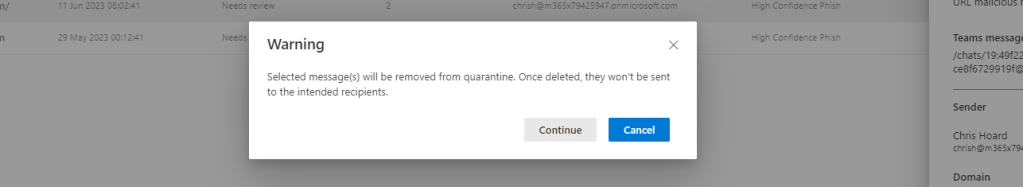
9.) Deleting the zapped message prevents delivery but does not clear the block notifications for the sender or the recipient
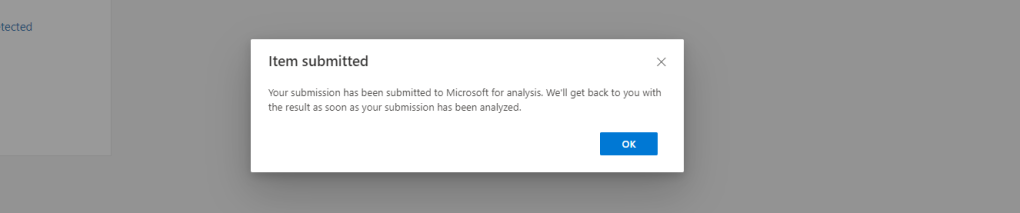
10.) Submitting the zapped message raises the message to Teams Messages within Submissions which is located under Actions and Submissions
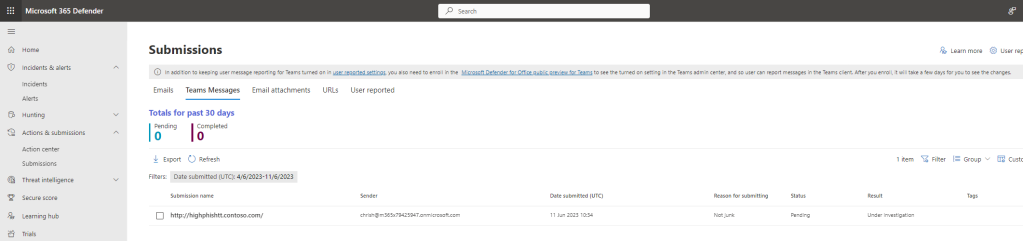
Our job here is done. Malicious messages have been zapped and as admins, we have taken action on those zapped messages, deleting them and sending them to Microsoft to review
AMENDING THE QUARANTINE POLICY
Some admins, for their own reasons, may not want to quarantine messages with ZAP with the default policies already in place. They may require a different action to take place when a message is zapped. This blog post will not drill through these different actions this time around, but it will show how to amend the quarantine policy.
1.) Select a zapped teams message in quarantine, and identify the quarantine policy. This example shows it as AdminOnlyAccessPolicy
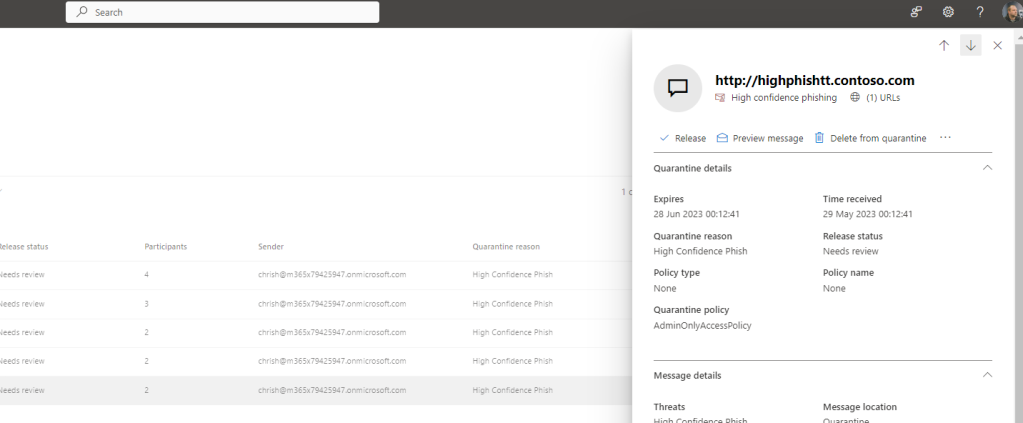
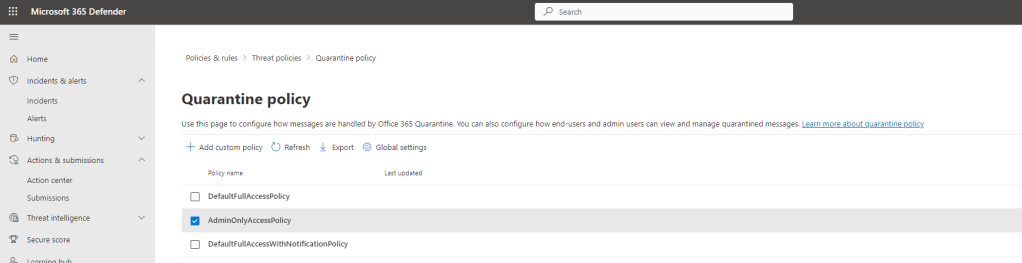
2.) In the M365 Defender Portal under Policies and Rules select Threat Policies and then Quarantine Policies

3.) Add a custom policy if required. The default policies cannot be modified.
An important development since initially writing this blog is that Microsoft have now released explicit cmdlets to modify a seperate Teams Protection Policy for ZAP which includes specifying the quarantine policies for both Malware and High Confidence Phishing. This is covered in a new blog written on 10/07/2023 which is now available – Teams Real Simple with Pictures: Configuring Zero Hour Auto Purge (ZAP) for Teams through PowerShell now in Preview
DISABLING ENABLING ZAP
Finally, how do we enable/disable ZAP for Teams? Like quarantine above, enabling and disabling ZAP for Teams is now done via PowerShell and amending the new Teams Protection Policy which came into force in July and which is seperate from ZAP for Exchange Online. This is covered in a new blog written on 10/07/2023 which is now available – Teams Real Simple with Pictures: Configuring Zero Hour Auto Purge (ZAP) for Teams through PowerShell now in Preview
CONCLUSION
Like the other components of CSMT ZAP is a solid add that when the gaps are filled (and I would expect them to be at some point in the future either prior to GA or not long after) it will be a very valuable addition to the Defender portfolio and the P2 licence. I hope you enjoyed this introduction and can go on to do your own testing where you may find additional behaviours and nuances. Best of luck!

