Back in the day - around the time I first started engaging with the Teams community - Microsoft introduced the ability to discover private teams. If I remember correctly, the first iteration of whether a private team was discoverable was set at the team level which could be toggled on or off whenever a team was created, or when it were edited. This allowed org users to see private teams which were defined as discoverable by team owners who chose to do so whether they wanted to make them discoverable or not. For sure, back then it wasn't in the Teams Admin Centre. The Teams Admin Centre didn't even exist as it was the combined Teams/SfB AC in those days. But sometime after it was released this functionality disappeared. Bizarre. It was probably the first time I'd seen something introduced into the Teams Client which was pretty substantial, only to see it removed. And nothing much was really made about it on the forums such as the Microsoft Tech Community either. So the question is why? I don't remember a reason being given. Maybe it just didn't work. Maybe it created issues for admins or orgs that used it, or a load of technical debt for Microsoft. More likely, there was a better way to do it in the future which was identified based on how other things were developing. And so it caught my eye this week in the Teams Admin Centre. Not the exact functionality per se since this functionality allows a user to discover all private teams in an org. But it's approximate. And as it turned out this is the first half of a full solution. The ability to set explicit teams as discoverable should be possible through sensitivity labelling via Microsoft Purview, but whether this gets us to where we want - as in labelled private teams are discoverable, the rest are not remains to be proven. This week, let's look at the ability to allow org users to search and see all private teams - since some orgs would actually want this. We'll then explore Purview in a seperate blog.
Category: Microsoft Teams
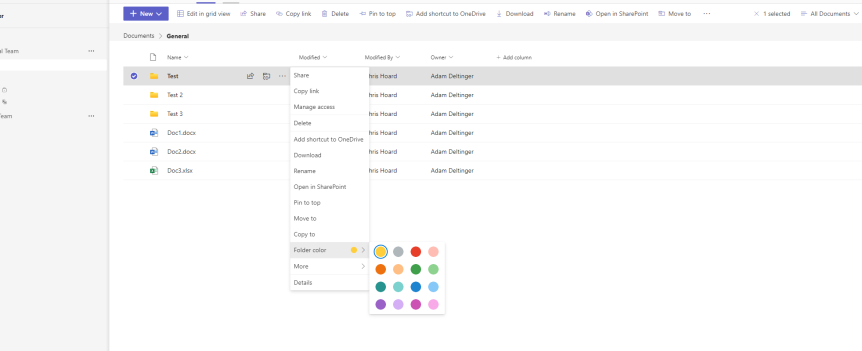
Teams Real Simple with Pictures: 5 File Management Features I’m enjoying in the New Teams
I'm not gonna lie; there hasn't been much left in the tank the past few weeks. I fully intended to have written this prior to the Super Bowl coverage last Sunday - but I decided to watch the game as its been full on with Copilot, Mesh, Sentinel, Defender for Cloud and all that other good stuff. I guess I could have easily written something about any one of those things. But when I do a lot of what I would call forward facing work, a part of me likes to almost pivot back to the fundamental adds because they can be missed, or overlooked, or they just don't grab the column inches when they could matter a great deal. I feel this way about the File experience in Teams. Sure, it's not the sexiest of things. It never was compared to, say, chat, or meetings, or calling. But I remember a time when you couldn't pin, let alone add columns or metadata through the Teams client. Now? The Files app is gone. The OneDrive app is here. And there's lots more we can do in Tabs. So here's 5 things I'm digging with file management today. I don't know when they came in. I wasn't looking. And the Super Bowl? I watched my first - think it was on Channel 4 - way back in 1989 as my dad was really into it. Super Bowl XXIII where the San Francisco 49's beat the Cincinnati Bengals. Joe Montana was Quarterback and Jerry Rice was the MVP. How odd that the 49ers were on again, another Super Bowl, when I started this blog 34 years later. The 49ers didn't make it. I didn't make the blog. But it was, after all, a hell of a game.
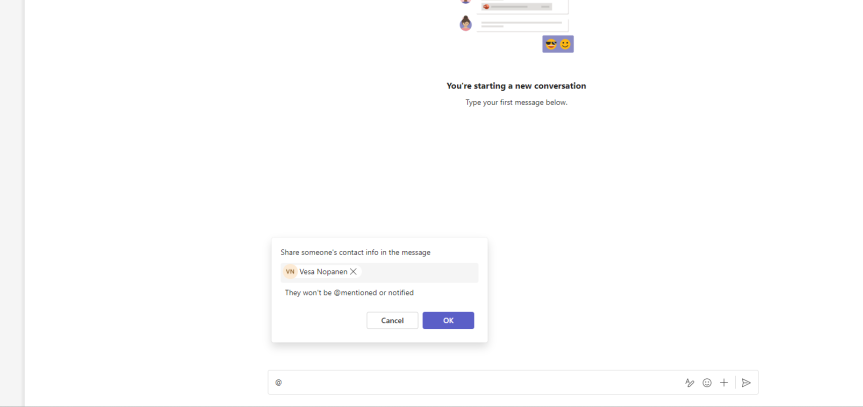
Teams Real Simple with Pictures: Share Contact Info, Domain Specific Search, Turn Off Activity Mails and Read By in Group Chat
After many years of writing I decided I needed a bit of an extended break from the blog. January has been unlike anything I have experienced over fifteen years in the Industry. Our firm is rolling out into multiple countries around Europe; I've been in Norway supporting that. But then there is Teams Nation 2024 in February (please register and help us spread the word), multiple CCP's and of course a little matter of that beast Copilot dropping into the market for CSP. All this adds up. 12-14 hour days haven't been uncommon and I had some load balancing to do. But now? I'm back. I hope you've been well. I have a lot to cover in the next few months. But today? As you would expect I'm using the new Teams client more than ever, and whilst I am still pushing Microsoft on an answer to saved messages (this is a key functionality for me) in the last month I have found some really nice adds which - kind of like the situation I've been in the past month - all add up. The first is the ability to share contact info in a chat: this is the contact info of others within the organisation (not an actual contact from the people app). It's proven useful rather than having to message or email contact info. The second is domain specific search, which is the ability to filter down searches from the search bar. Again nice timesaver. Third - and this is one which I love is the ability to easily turn off Missed Activity mails. I don't want more mail. I'll go get it out of the activity feed without having to cross check. And finally, the ability to see exactly who has read a message in a group chat. Now since I've been away a bit these may be new - and they may not - and I don't think I've written about them previously, but bear with me as I get back on the horse.
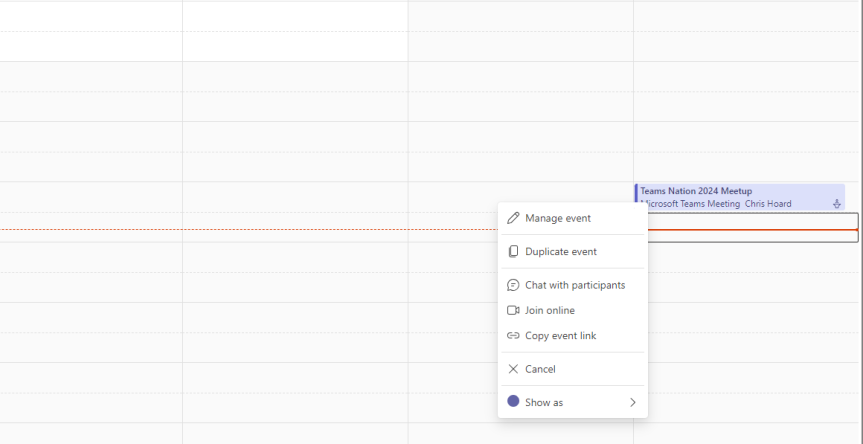
Teams Nation is back! Join us! A Q&A to get you up to speed
Yes, Teams Nation is back! And as we have just opened the registration, let me take the time to bring you up to speed.